JavaScript security in 2025: practical threats and what you must change today
Read this and you'll walk away with a clear map of the biggest JavaScript risks heading into 2025, the attack patterns cybercriminals are favoring, and an actionable checklist you can use right now to reduce your app's exposure.
Why JS security looks different in 2025
JavaScript applications today operate across serverless endpoints, CI/CD pipelines, third-party delivery networks, WebAssembly modules, and AI-powered code generation. This expanding attack surface enables adversaries to insert malicious logic into your running application without modifying the source repository.
Supply chain and dependencies: beyond CVEs
The single biggest persistent risk is the ecosystem of packages, transitive dependencies, and package managers that your build relies on.
Transitive dependency risk: a vulnerability in a deep transitive package can compromise your app even if direct dependencies are clean (see NIST’s Supply Chain Risk Management Practices for Federal Information Systems ).
Package manager compromise: attackers have targeted npm registries and CI credentials to publish malicious releases; protect publish tokens and use least privilege.
Dependency confusion / typosquatting: attackers have successfully published malicious packages that mimic private package names and relied on misconfigured resolution orders to get those packages installed in enterprise builds.
Risk Category | Description | Mitigation Strategy |
|---|---|---|
Transitive dependency risk | Deep package vulnerability compromising app | Pin direct dependencies and require signed provenance |
Package manager compromise | Malicious releases via npm registry or CI token theft | Protect publish tokens, rotate credentials, use least privilege |
Dependency confusion / typosquatting | Attackers publish similarly named packages to hijack installs | Enforce strict registry configuration and namespaces |
What to do
Pin direct dependencies, monitor transitive updates, and require provenance (signed packages or verified publishers) for critical dependencies (learn about Sigstore’s package signing ).
Enforce strict registry configuration and namespace protections to block typosquatting and dependency confusion.
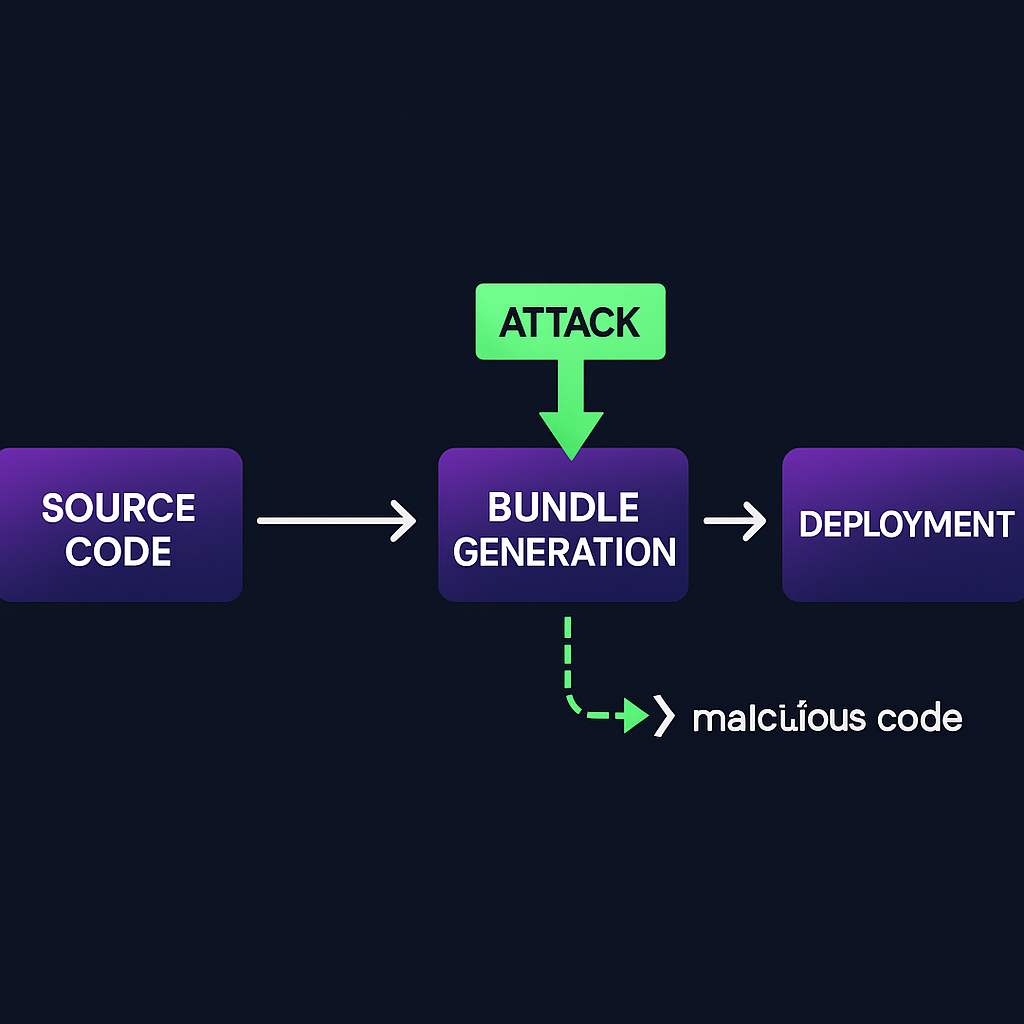
Bundles, minification, and the rise of “bundle poisoning”
Modern builds shove dozens or hundreds of packages into a single minified bundle. That consolidation reduces observability: a tiny injected change in a bundle can run everywhere without showing up in source code history.
Bundle poisoning: attackers who compromise build tooling, CI credentials, or a pipeline step can inject malicious code directly into the generated bundle without changing tracked source files.
Source maps and minification: shipping source maps to production can reveal code and structure to attackers; omitting them reduces debugging, but shipping them incorrectly leaks code.
What to do
Treat build artifacts as sensitive supply-chain outputs: sign them, store them in an immutable artifact repository, and verify artifact signatures during deployment.
Harden CI/CD: rotate and scope tokens, add step-level attestations, and run reproducible builds so you can re-produce a bundle from a commit to validate integrity.
AI-generated code: useful, but risky in subtle ways
AI coding assistants accelerate development but introduce new security failure modes.
Hallucination exploits: LLMs can produce plausible-looking but insecure constructs—unsafe eval(), lax input validation, SSRF-prone fetches, or open redirects—that human reviewers may miss because the code looks idiomatic.
Attackers leveraging AI: adversaries can use AI assistants themselves to craft context-aware exploit code tailored to a target app’s patterns, increasing the accuracy and stealth of payloads.
What to do
Treat AI-generated contributions like untrusted third-party code: require the same static analysis, dependency checks, and test coverage before merging.
Add targeted security test cases for common AI hallucination classes (e.g., unsafe dynamic eval, incomplete auth checks, unsanitized URL redirects).
CDNs, unpinned imports, and delivery network abuse
Including libraries from public CDNs with wildcard or unpinned versions gives attackers a fluid avenue to serve backdoored code.
Wildcard imports: importing jQuery@* or using unpinned CDN URLs lets an attacker who controls a package’s distribution or a CDN cache injure many sites quickly.
CDN misuse: attackers can abuse content delivery networks or injection points to serve modified versions of popular libraries; apps that don’t verify integrity are vulnerable.
What to do
Use Subresource Integrity (SRI) with pinned cryptographic hashes for externally hosted scripts, or host critical libs yourself from an internal, signed artifact store.
Avoid wildcard versions in package.json; use automated tooling to approve dependency changes.
Framework defaults, auto-generated endpoints, and server functions
Modern frameworks (Next.js, SvelteKit, React Server Components) reduce boilerplate—but they also create convention-based endpoints and server functions that can be exposed without explicit handling.
Auto-generated endpoints: framework conventions can create publicly accessible routes or server handlers that developers assume are private, leading to missing auth and validation by default.
Framework-by-default vulnerabilities: insecure defaults (for example, permissive CORS or deserialization) can silently expose large swaths of apps until a critical vulnerability is revealed.
What to do
Audit all framework-generated routes and server functions as part of code reviews—assume “convention = public” unless explicitly protected.
Add automated checks to detect unprotected handlers or endpoints lacking proper auth and input validation.
Hidden build-time risks: stale devDependencies and toolchain RCEs
A surprising number of incidents stem from build tools and devDependencies that were never intended to ship but still run in CI or production build contexts.
Stale devDependencies: old versions of bundlers, transpilers, or test runners with known RCEs remain attackable if they run in CI or are accidentally packaged into production builds.
Malicious polyfills/ponyfills: legacy code may pull in polyfills from untrusted sources; attackers can target these to create subtle data exfiltration or bypasses.
What to do
Scan devDependencies as rigorously as production deps and remove or update unused build tools.
Separate build/runtime environments so dev tools do not execute in production contexts; apply the principle of least privilege to build machines (see Docker’s guidance on container security (https://docs.docker.com/engine/security/)).
WebAssembly and obfuscated payloads
WebAssembly (WASM) is powerful, but it also gives attackers a stealth layer: compiled modules are harder to inspect than JS.
WASM as a stealth vector: attackers can place obfuscated or dynamically generated WASM modules behind innocuous JS loaders; static scanning of JS won’t reveal payloads in the same way.
Third-party WASM: fetching WASM modules from external sources or generating them at runtime increases risk.
What to do
Treat WASM artifacts like binaries: verify provenance, run sandboxed dynamic analysis, and require signed delivery for third-party modules.
Practical checklist you can implement this week
Checklist Item | Action Details |
|---|---|
1 | Pin dependencies, set up automated scans, and require signed artifacts for key packages. |
2 | Secure CI/CD: rotate secrets, limit publish scopes, require attestations, and store artifacts immutably. |
3 | Use SRI and pin CDN imports, or internally host trusted copies of third-party assets. |
4 | Treat AI-generated code as external: run static analysis, unit tests, and security checks pre-merge. |
5 | Audit endpoints and server functions created by frameworks for missing authentication and validation gaps. |
6 | Scan developer dependencies, remove unused tools, and clearly separate build and runtime permissions. |
7 | Verify/sign WebAssembly modules and run dynamic analysis on all third-party binary artifacts. |
8 | Maintain an incident playbook, covering detection/response for bundle tampering and package registry typosquatting attacks. |
“Supply-chain attacks often target the weakest link — a developer’s workstation, a misconfigured registry, or a CI token. Treat every tool in your pipeline as part of your security perimeter.”
A smarter perimeter: shift-left, verify-right
You can’t stop attackers by just patching dependencies after the fact. The most resilient JavaScript defenses are built on three commitments: move security left into development (code reviews, automated tests, AI-awareness), verify artifacts and delivery paths (signed builds, SRI, provenance), and restrict build/runtime privileges (CI hardening, isolated runtime). Combine those with continuous monitoring for unusual changes in registries, build artifacts, and CDN content and you’ll close the gaps attackers are actively exploiting in 2025.
Take one concrete action today: pick your top three third-party packages and enable automated provenance checks or pin their delivery hashes. That small step stops a large class of supply-chain and CDN attacks before they ever reach production.
:format(webp))
:format(webp))
:format(webp))
:format(webp))